
You’ve built the firewall. Secured the endpoints. Trained your teams.
But what if someone’s already inside?
Every device on your network is a door. Network Access Control (NAC) makes sure only the right ones get a key.
At BCS Technologies, we help businesses across Dubai, Abu Dhabi, Riyadh, and Doha lock down unauthorized access with intelligent, identity-driven NAC solutions—tailored for compliance, scalability, and control.
Zero Trust starts here.
If you can’t see it, you can’t protect it.
Today’s enterprise networks are no longer behind four walls. Devices connect from anywhere—BYOD laptops, contractor tablets, IoT sensors, and cloud apps. That’s not a risk you can afford to leave unguarded.
Threats NAC Stops in Real Time:
Unregistered or rogue devices trying to connect
Non-compliant or unpatched endpoints
Guest users bypassing security protocols
Devices lacking antivirus, encryption, or updates
Internal users accessing sensitive zones unintentionally
NAC acts as a real-time traffic controller—blocking, allowing, and segmenting devices based on your rules. No guesswork. No manual checks.
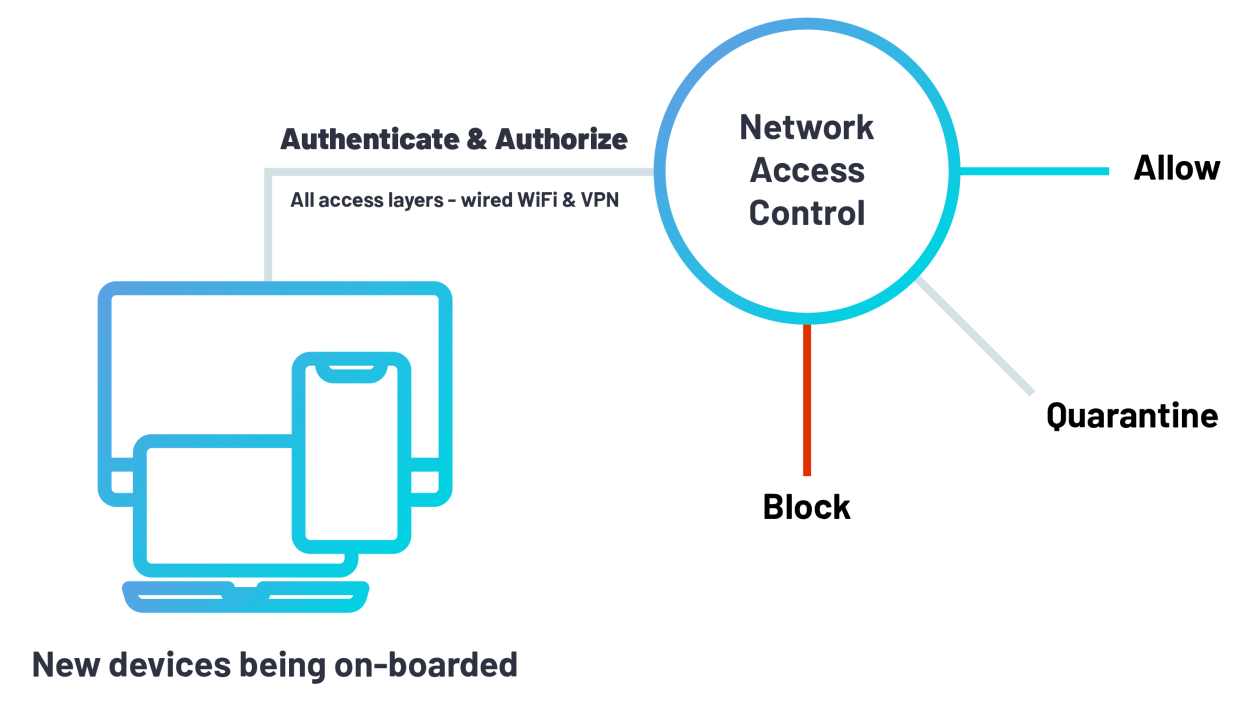
We don’t do basic installs. We engineer Zero Trust Network Access foundations, designed around your users, policies, and compliance needs.
1. Total Network Visibility
Discover and classify every device—managed or unmanaged—before it even gets access.
2. Identity-Based Authentication
Integrate with your Active Directory, HRMS, and MDM platforms. Devices must match identity, role, and health posture.
3. Endpoint Compliance Checks
BCS NAC scans for OS updates, AV status, encryption, and other posture checks before allowing access.
4. Dynamic Access Segmentation
Grant access to what’s needed—nothing more. Sales doesn’t see Finance. Guests stay in the guest zone.
5. Real-Time Alerts + Quarantine
Instantly isolate risky devices and notify IT. We integrate with SIEMs and incident response tools.
.png)
NAC Strategy, Not Just Software
We tailor access policies to business logic—not just install a platform.
Tech-Agnostic + Fully Integrated
Whether you’re on Cisco ISE, FortiNAC, Aruba ClearPass, or something else—we integrate seamlessly.
Built for GCC Regulations
We’re fluent in NCA ECC, PDPL, QCB, and international frameworks like ISO 27001.
Live 24/7 Monitoring & Optimization
Post-deployment, we stay in the loop. NAC is a journey, not a one-time config.
- Zero trust, built into your network access
- Improved compliance & audit readiness
- Risk-based access control by user, role & device
- Reduced insider threat & lateral movement risk
- Seamless guest & contractor access, without risk
- Full visibility, finally

– IT Director, Financial Institution, KSA
It’s time to move from guesswork to granular, verified access control. Whether you're looking to start with discovery or deploy a full NAC framework—
BCS Technologies is your trusted Network Access Control partner in the UAE, Qatar, and Saudi Arabia.
- Get Started Now
- Schedule a Free NAC Discovery Call
- Get a Custom Network Access Blueprint
- Talk to a Security Engineer Today


BCS has over 15 years of experience in designing and implementing cybersecurity solutions to various verticals such as oil and gas, FMCG, manufacturing, retail, packaging, hospitality, healthcare, rea...

In today’s digital landscape, cyber threats are more sophisticated than ever, making endpoint security solutions in Dubai, UAE a critical necessity for businesses. With remote work, cloud adopti...

In today’s hybrid work era, users access data from anywhere, using any device—and the traditional network perimeter no longer exists. That’s why forward-thinking organizations in the...

BCS has over 15 years of experience in designing and implementing cybersecurity solutions to various verticals such as oil and gas, FMCG, manufacturing, retail, packaging, hospitality, healthcare, rea...